Few static analyses make their way to the real-world due to the unrealistic assumptions that they make. I am interested in developing and evaluating various program analysis techniques that can be used in practice by exploring three aspects: scalability, precision, and usability. My interests span programming languages, software systems, and software engineering.
Below is a list of my current and inactive projects.
Current Projects

SWAN (2017–)











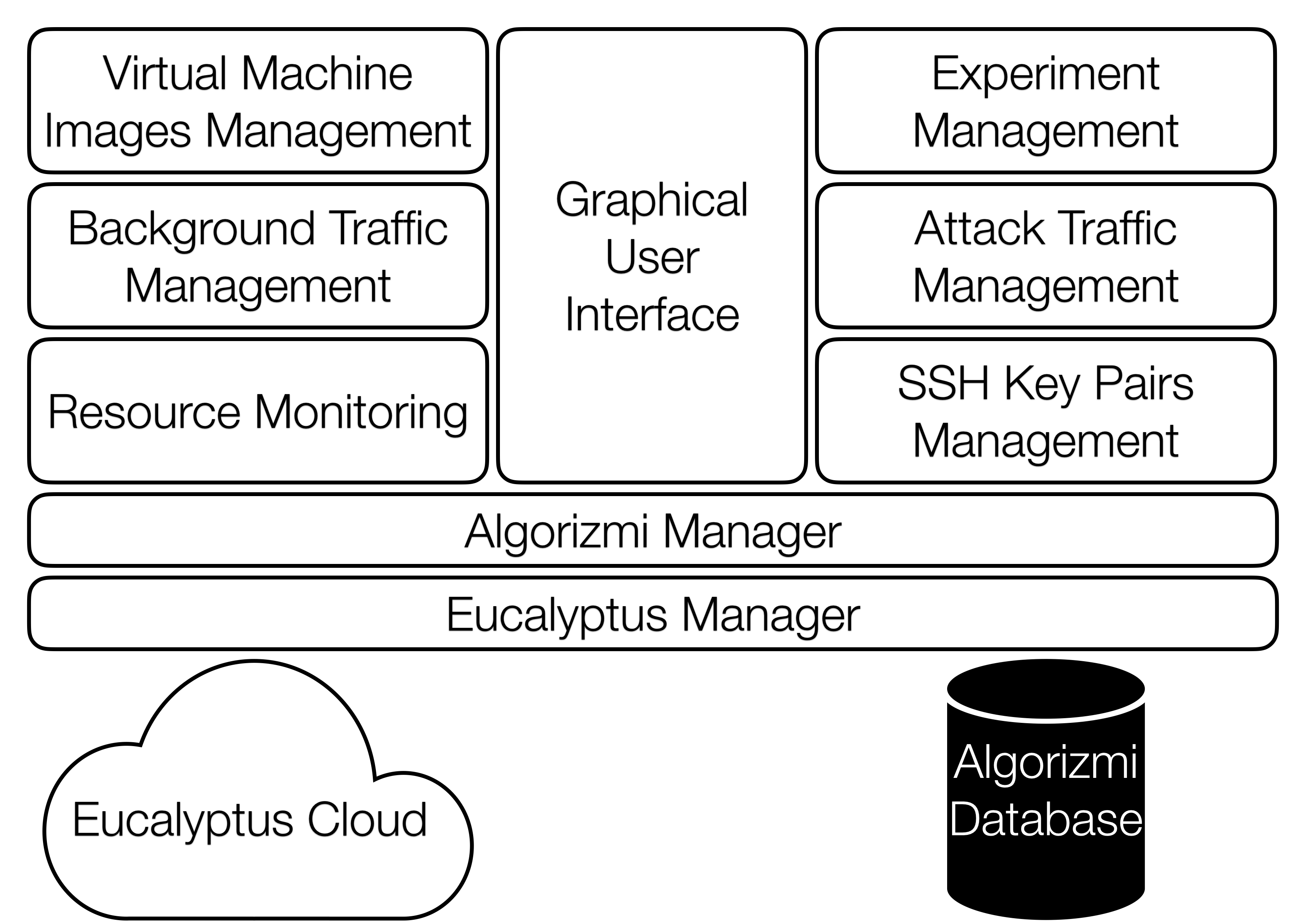
Can I detect security vulnerabilities in my Swift app? In this work, we have been developing SWAN, a program analysis framework for Swift programs based on SPDS . The framework enables various deep static analyses, from finding API misuses using typestate analysis to detecting security vulnerabilities using taint analysis.
Just-in-Time Compilers (2016–)







Can we help JIT compilers make better decisions when applying a code transformation? In this work, we have been developing several algorithms that enable a JIT compiler to reason not only about the cost of applying a code tranformation (e.g., method inlining), but also about the potential future benefits (e.g., further optimizations) of applying such a code transformation.
Inactive Projects

Usability of Static Analysis Tools (2014–2021)







How can we build better experiences for users of static analysis tools? In this work, we have been exploring novel techniques to facilitate the development of program analyses that are more responsive, more precise, well-integrated in the developer's workflow, and customized to the developer's needs.

Detecting Misuses of Crypto APIs (2015–2020)




Can program analysis help developers use crypto APIs more securely? In this work, we have been working on an end-to-end solution to detect misuses of crypto APIs that provides a DSL to define the correct uses of an API, a compiler that generates static analysis checks based on those rules, and IDE extensions that help developers detect misuses in their code based on our infrastructure. Most recently, our work with CogniCrypt helped Symantec fix a bug in one of its products that could lead to privilege escalation.

Scalable and Precise Pointer Analysis (2014–2020)



Can pointer analysis be both scalable and precise? In this work, we explore how to leverage the advantages of distributive frameworks such as IFDS, IDE, and WPDS to perform scalable and precise non-distributive analyses such as pointer analysis. We have been building various on-demand pointer analyses that also encode rich alias information for the queried variables.
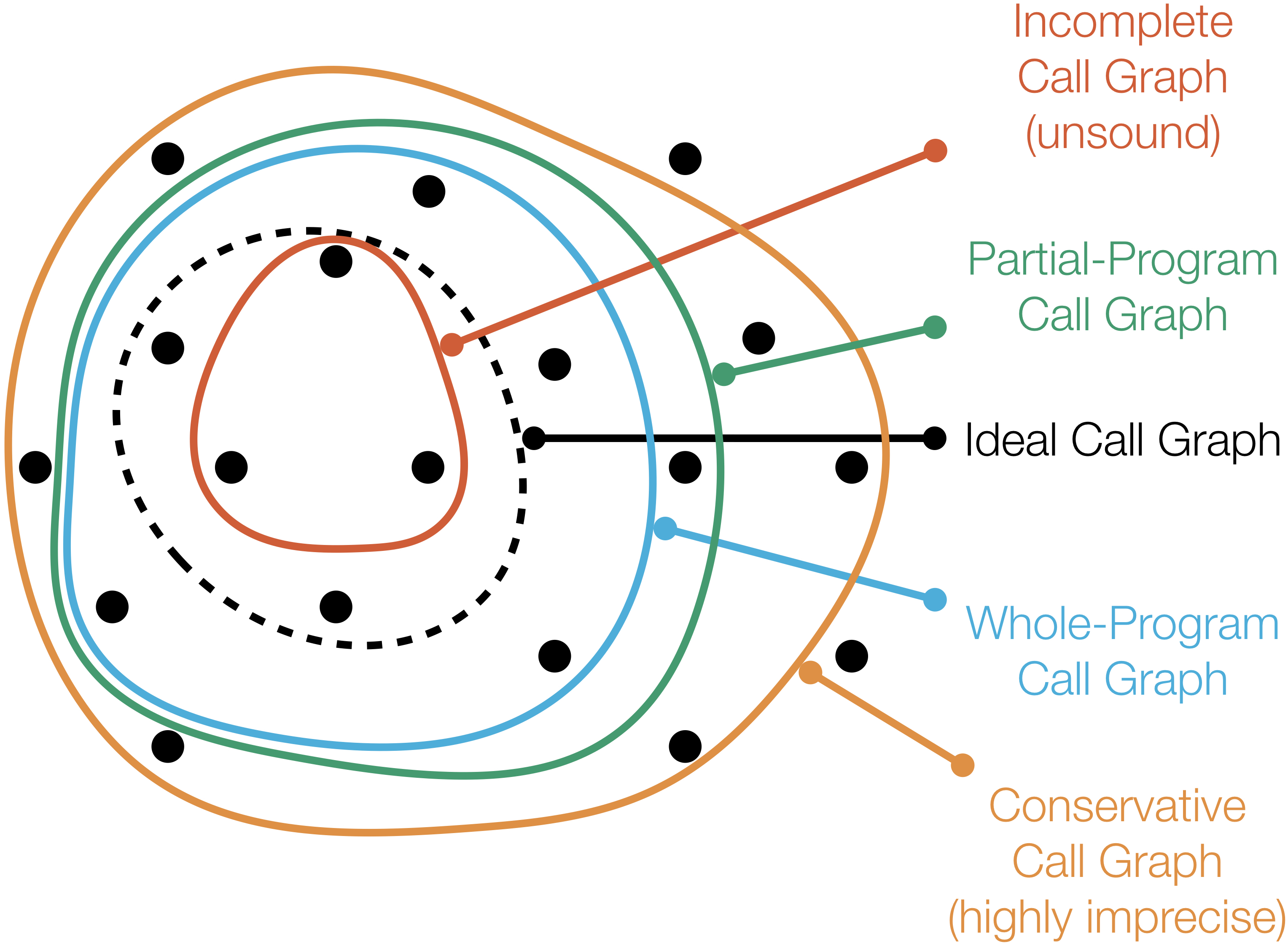
Partial-Program Analysis for Java (2010–2020)



Can we perform whole-program analysis of a given Java application without analyzing the whole program? Through light-weight static analyses of the structure of a given application, we have shown that the answer to this question is 'yes'. Moreover, we developed Averroes, a placeholder library generator that enables the use of that suite in any Java whole-program analysis framework. Using Averroes reduces the amount of code that needs to be analyzed by up to 600x, improving the performance of call graph analysis as it becomes up to 7x faster, and uses up to 6x less memory. Averroes is currently used by the major Java static analysis frameworks, Soot, WALA, and DOOP.
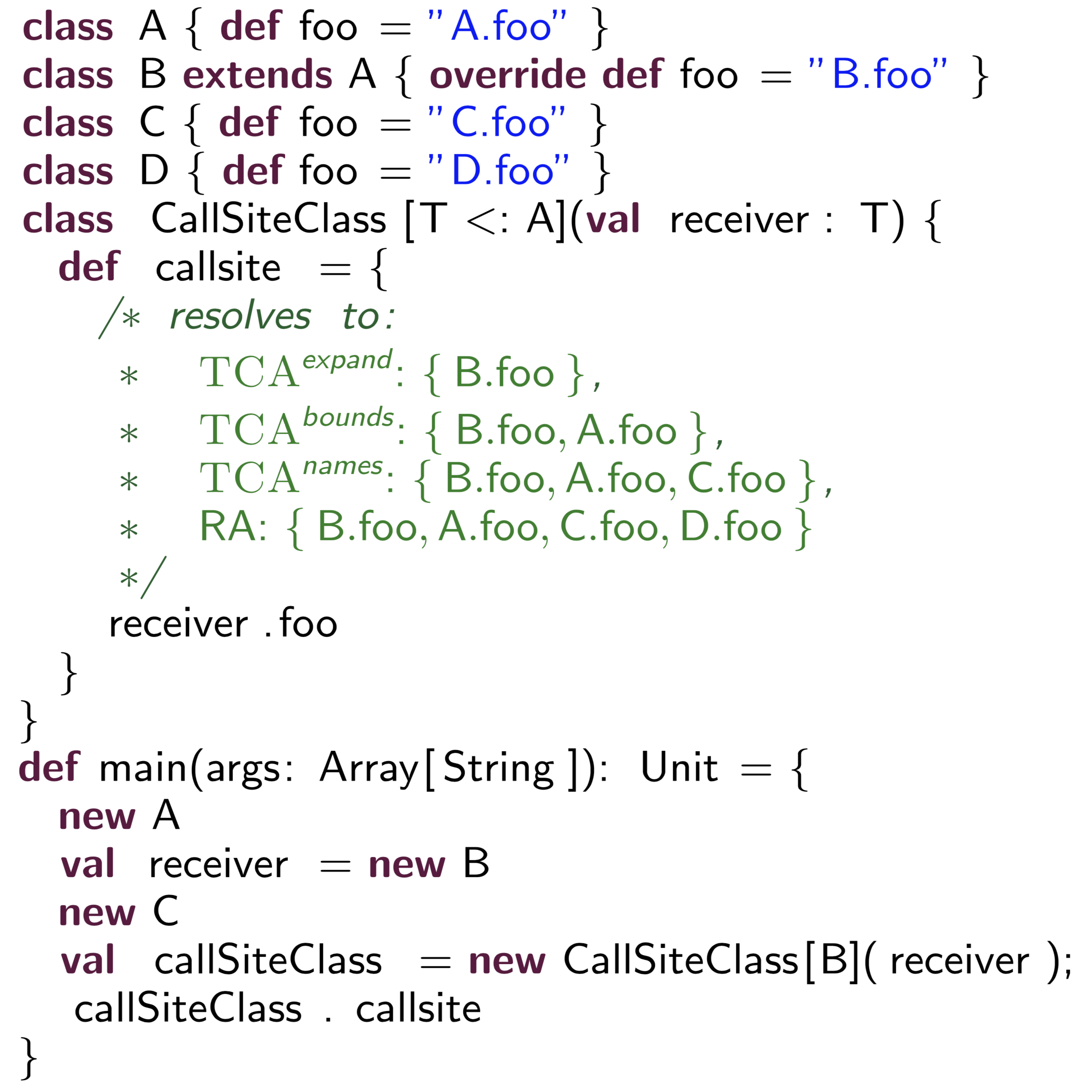
ScalaCG (2013–2015)

Is analyzing the Scala source code any different than analyzing the JVM bytecodes that the Scala compiler generates? In this work, we developed ScalaCG, a collection of low-cost call graph analyses that target the Scala source code and support various Scala features such as traits, abstract type members, closures, and path-dependent types. Using ScalaCG produces call graphs that are up to 19x more precise than using a bytecode-based approach in terms of call edges and reachable nodes. ScalaCG was awarded a Distinguished Artifact Award at the European Conference on Object-Oriented Programming (ECOOP) in 2014. Scalacg has been extended by the original Scala research group at EPFL to improve call graph precision and decrease analysis time for non-trivial Scala programs. These extensions are integrated in the upcoming Scala Dotty compiler.